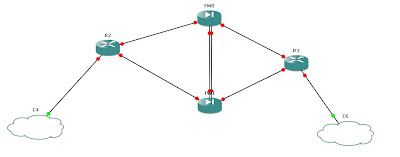
Consider this type of scenario shown below:
Components used:
Cisco PIX 525 with 8.0 version.
c3600 router with 16ESW module for emulating as layer 3 switch.
Lower half is configured with GLBP and upper half is configured with HSRP.
Why I used both protocols? So that anybody wants to know about the mechanics how they work can able to check configuration of both protocols. ethernet 2 of both firewalls is used as management interface.
Briefings of both protocols:
- Both are cisco proprietory.
- They can do interface monitoring so that is any interface fails or active router or L3 switch goes down switchover will take place.
- GLBP is somewhat different than HSRP in one feature that it provides loadbalancing among gateways. Can be on host based mac address, Round Robin Loadbalancing(default) or weighted.
Ofcourse, I have used failover on both firewalls FW0(Active) and FW1(Standby) for redundancy purpose.
Before configuring firewall always remember these points:
- Firewall model should be same
- No. of interfaces must be same
- OS version should be same
- Memories should be same
- For more you can refer to http://www.cisco.com/
You can go through BCMSN guide for further studies. I will not explain too much.
Configuration part:
FW0(PRIMARY) configuration:
!
hostname FW0
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif Outside
security-level 0
ip address 192.168.10.250 255.255.255.0
!
interface Ethernet1
nameif Inside
security-level 100
ip address 192.168.200.1 255.255.255.0
!
interface Ethernet2
nameif mgmt
security-level 99
ip address 192.168.4.253 255.255.255.0 standby 192.168.4.254
management-only
!
interface Ethernet3
!
interface Ethernet4
!
interface Redundant1
description LAN/STATE Failover Interface
member-interface Ethernet3
member-interface Ethernet4
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list Outside_access_in extended permit icmp any any
pager lines 24
mtu Outside 1500
mtu Inside 1500
mtu mgmt 1500
failover
failover lan unit primary
failover lan interface fail_int Redundant1
failover lan enable
failover polltime unit msec 200 holdtime msec 800
failover polltime interface msec 500 holdtime 5
failover key *****
failover link fail_int Redundant1
failover interface ip fail_int 1.1.1.1 255.255.255.252 standby 1.1.1.2
no monitor-interface mgmt
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
global (Outside) 1 interface
nat (Inside) 1 0.0.0.0 0.0.0.0
access-group Outside_access_in in interface Outside
route Outside 0.0.0.0 0.0.0.0 192.168.10.254 1
route Inside 192.168.56.0 255.255.255.0 192.168.200.100 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.4.0 255.255.255.0 mgmt
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
dhcp-client broadcast-flag
threat-detection basic-threat
threat-detection statistics access-list
!
!
prompt hostname context
Cryptochecksum:2dba6cd4479e3e98aa10893eec4c2862
: end
FW1(SECONDARY) configuration:
PIX Version 8.0(2)
!
hostname FW0
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif Outside
security-level 0
ip address 192.168.10.250 255.255.255.0
!
interface Ethernet1
nameif Inside
security-level 100
ip address 192.168.200.1 255.255.255.0
!
interface Ethernet2
nameif mgmt
security-level 99
ip address 192.168.4.253 255.255.255.0 standby 192.168.4.254
management-only
!
interface Ethernet3
!
interface Ethernet4
!
interface Redundant1
description LAN/STATE Failover Interface
member-interface Ethernet3
member-interface Ethernet4
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list Outside_access_in extended permit icmp any any
pager lines 24
mtu Outside 1500
mtu Inside 1500
mtu mgmt 1500
failover
failover lan unit secondary
failover lan interface fail_int Redundant1
failover lan enable
failover polltime unit msec 200 holdtime msec 800
failover polltime interface msec 500 holdtime 5
failover key *****
failover link fail_int Redundant1
failover interface ip fail_int 1.1.1.1 255.255.255.252 standby 1.1.1.2
no monitor-interface mgmt
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
global (Outside) 1 interface
nat (Inside) 1 0.0.0.0 0.0.0.0
access-group Outside_access_in in interface Outside
route Outside 0.0.0.0 0.0.0.0 192.168.10.254 1
route Inside 192.168.56.0 255.255.255.0 192.168.200.100 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.4.0 255.255.255.0 mgmt
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
dhcp-client broadcast-flag
threat-detection basic-threat
threat-detection statistics access-list
!
!
prompt hostname context
Cryptochecksum:da40a422579a902a3ccf7899907ba015
: end
R0(GLBP ACTIVE) configuration:
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
spanning-tree vlan 1 priority 8192
spanning-tree vlan 99 priority 8192
!
!
!
!
!
!
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
switchport access vlan 99
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
no switchport
ip address 192.168.56.2 255.255.255.0
glbp 1 ip 192.168.56.254
glbp 1 priority 150
glbp 1 preempt
!
interface FastEthernet1/14
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface FastEthernet1/15
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface Vlan1
no ip address
!
interface Vlan99
ip address 192.168.200.254 255.255.255.0
glbp 2 ip 192.168.200.100
glbp 2 priority 150
glbp 2 preempt
glbp 2 authentication md5 key-string cisco
!
!
ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 Vlan99 192.168.200.1
!
!
!
mac-address-table static 0007.b400.0202 interface FastEthernet1/15 vlan 99
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end
R1(GLBP STANDBY) Configuration:
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
vtp file nvram:vlan.dat
!
!
!
!
!
!
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
switchport access vlan 99
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
no switchport
ip address 192.168.56.3 255.255.255.0
glbp 1 ip 192.168.56.254
glbp 1 timers 1 2
glbp 1 preempt
!
interface FastEthernet1/14
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface FastEthernet1/15
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface Vlan1
no ip address
!
interface Vlan99
ip address 192.168.200.253 255.255.255.0
glbp 2 ip 192.168.200.100
glbp 2 preempt
glbp 2 authentication md5 key-string cisco
!
!
ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 Vlan99 192.168.200.1
!
!
!
mac-address-table static 0007.b400.0201 interface FastEthernet1/15 vlan 99
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end
R3(HSRP ACTIVE) Configuration:
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
spanning-tree vlan 1 priority 8192
spanning-tree vlan 99 priority 8192
vtp file nvram:vlan.dat
!
!
!
!
!
!
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
switchport access vlan 99
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
no switchport
ip address 192.168.1.252 255.255.255.0
standby 3 ip 192.168.1.254
standby 3 timers 1 3
standby 3 priority 150
standby 3 preempt
!
interface FastEthernet1/14
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface FastEthernet1/15
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface Vlan1
no ip address
!
interface Vlan99
ip address 192.168.10.1 255.255.255.0
standby 4 ip 192.168.10.254
standby 4 timers 1 3
standby 4 priority 150
standby 4 preempt
standby 4 authentication md5 key-string cisco
!
!
ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.168.1.1
!
!
!
mac-address-table static 0000.0c07.ac04 interface FastEthernet1/15 vlan 99
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end
R2(HSRP STANBY) Configuration:
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
vtp file nvram:vlan.dat
!
!
!
!
!
!
!
interface Port-channel1
switchport trunk native vlan 99
switchport mode trunk
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
switchport access vlan 99
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
no switchport
ip address 192.168.1.253 255.255.255.0
standby 3 ip 192.168.1.254
standby 3 timers 1 3
standby 3 preempt
!
interface FastEthernet1/14
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface FastEthernet1/15
switchport trunk native vlan 99
switchport mode trunk
channel-group 1 mode on
!
interface Vlan1
no ip address
!
interface Vlan99
ip address 192.168.10.2 255.255.255.0
standby 4 ip 192.168.10.254
standby 4 timers 1 3
standby 4 preempt
standby 4 authentication md5 key-string cisco
!
!
ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.168.1.1
!
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end