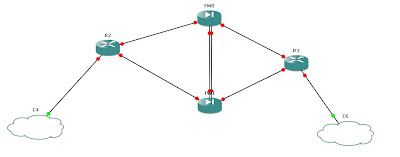
Configuration according to diagram.
As with all cisco firewall the rule of thumb is traffic traverse from higher security level to lower security level, without applying any ACL whereby applying only nat or no nat-control(i.e. only with routing suffices without any translation). If outside hosts(lower security level) want to initiate connection to inside host(higher security level), appliance must have static nat and ACL configured. As of above scenario, I used nat-control. Inside network in network diagram is right side of firewalls (security level 100) and outside network is left side of firewalls(security level 0). Failover is configured on FW0 and FW1.
How is host on the same computer is connected in inside network?
This was done via VMWARE OS and given default gateway ip of failover ip of firewalls. Interesting feature of failover is when you try to configure Active appliance(FW1) and save it. It replicates to standby firewall(FW0) for e.g. ip addresses of interfaces, routing, natting etc. In other words, they are mirror of each other.
So here is the configuration for FW1(Active):
PIX Version 8.0(2)
!
hostname PIXDOWN
domain-name domain.local
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 192.168.1.250 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 192.168.56.2 255.255.255.0
!
interface Ethernet2
description Management Interface
nameif MGMT_INT
security-level 99
ip address 192.168.200.1 255.255.255.0
management-only
!
interface Ethernet3
nameif DMZ
security-level 50
ip address 10.81.200.1 255.255.255.252 standby 10.81.200.2
!
interface Ethernet4
description LAN/STATE Failover Interface
!
passwd 2KFQnbNIdI.2KYOU encrypted
banner motd This is CISCO PIX 525
ftp mode passive
clock timezone IST 5 30
dns server-group DefaultDNS
domain-name domain.local
access-list outside_access_in extended permit icmp any any echo-reply
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit icmp any any traceroute
pager lines 24
logging enable
logging standby
logging asdm errors
mtu outside 1500
mtu inside 1500
mtu MGMT_INT 1500
mtu DMZ 1500
failover
failover lan unit primary
failover lan interface LANFAIL Ethernet4
failover lan enable
failover polltime unit 5 holdtime 15
failover replication http
failover link LANFAIL Ethernet4
failover interface ip LANFAIL 10.81.199.1 255.255.255.252 standby 10.81.199.2
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 192.168.1.20
global (outside) 1 192.168.1.21
nat (inside) 1 0.0.0.0 0.0.0.0 tcp 0 25 udp 25
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.1.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.56.0 255.255.255.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet 192.168.56.1 255.255.255.255 outside
telnet timeout 5
ssh scopy enable
ssh 192.168.56.1 255.255.255.255 outside
ssh timeout 5
console timeout 0
dhcpd address 192.168.200.10-192.168.200.254 MGMT_INT
dhcpd enable MGMT_INT
!
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
<--- More --->.
No Response from Mate
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
ntp authenticate
ntp server 207.46.232.182 prefer
username admin password f3UhLvUj1QsXsuK7 encrypted privilege 15
prompt hostname context
Cryptochecksum:27b6669bbc3bab31a8254dca80e44377
: end
Here is the configuration for FW0(Standby):
PIX Version 8.0(2)
!
hostname PIXDOWN
domain-name domain.local
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0
nameif outside
security-level 0
ip address 192.168.1.250 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 192.168.56.2 255.255.255.0
!
interface Ethernet2
description Management Interface
nameif MGMT_INT
security-level 99
ip address 192.168.200.1 255.255.255.0
management-only
!
interface Ethernet3
nameif DMZ
security-level 50
ip address 10.81.200.1 255.255.255.252 standby 10.81.200.2
!
interface Ethernet4
description LAN/STATE Failover Interface
!
passwd 2KFQnbNIdI.2KYOU encrypted
banner motd This is CISCO PIX 525
ftp mode passive
clock timezone IST 5 30
dns server-group DefaultDNS
domain-name domain.local
access-list outside_access_in extended permit icmp any any echo-reply
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit icmp any any traceroute
pager lines 24
logging enable
logging standby
logging asdm errors
mtu outside 1500
mtu inside 1500
mtu MGMT_INT 1500
mtu DMZ 1500
failover
failover lan unit secondary
failover lan interface LANFAIL Ethernet4
failover lan enable
failover polltime unit 5 holdtime 15
failover replication http
failover link LANFAIL Ethernet4
failover interface ip LANFAIL 10.81.199.1 255.255.255.252 standby 10.81.199.2
icmp unreachable rate-limit 1 burst-size 1
asdm image flash:/asdm-602.bin
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 192.168.1.20
global (outside) 1 192.168.1.21
nat (inside) 1 0.0.0.0 0.0.0.0 tcp 0 25 udp 25
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 192.168.1.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.56.0 255.255.255.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet 192.168.56.1 255.255.255.255 outside
telnet timeout 5
ssh scopy enable
ssh 192.168.56.1 255.255.255.255 outside
ssh timeout 5
console timeout 0
dhcpd address 192.168.200.10-192.168.200.254 MGMT_INT
dhcpd enable MGMT_INT
!
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
ntp authenticate
ntp server 207.46.232.182 prefer
username admin password f3UhLvUj1QsXsuK7 encrypted privilege 15
prompt hostname context
Cryptochecksum:a1c86e0759da13e6ca07ec971350e88a
: end
And on both routers I configured bridging on interfaces F0/0 and vlan 1
Here is the configuration for both router and is nearly same for both. Oh! by the way used cisco 3660 with ESW module
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
bridge irb
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
bridge-group 1
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
!
interface FastEthernet1/15
!
interface Vlan1
no ip address
bridge-group 1
!
interface BVI1
ip address dhcp
!
!
ip http server
no ip http secure-server
!
!
!
!
!
!
!
control-plane
!
bridge 1 protocol ieee
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end
No comments:
Post a Comment