Saturday, November 20, 2010
Configuring voip with CME 3.3 tunnelling voice traffic on IPSEC based site-to-site VPN
Here in this scenario I configured IPSEC based site-to-site VPN. Motivation for creating VPN is that I want to make my voip traffic encrypted on public network. 10.10.10.0/24 subnet is assumed to be public network. Here in network diagram R2,R3 and FW1 are enabled for IPSEC site-to-site VPN. Below is the configuration of all devices which I configured.
Here in this scenario three site are involved in VPN. Where GW is behind firewall. and other sites are c1 and c2 where cisco phone are located. With E.164 numbers configured 100 and 101. Dial peers are configured on R2 and R3. Telephony service is configured on R1 for two IP Phone can only communicate.
Wednesday, August 18, 2010
How to connect two links between cisco asa 5510 and cisco asa 5505
Now this scenario depicts that two cisco firewalls are connected which each other. And want to connect both firewalls wih dual links. But problem is cisco asa 5505 supports VLAN concept. And only let you interact to its interface via vlan only. There is no way to access interface directly or convert interface to layer 3 mode. And cisco asa 5510+ doesn't support vlan concept directly on its interface. If you would configure cisco asa 5510+ interfaces can do directly. As there is no vlan concept hence there is no port membership and so there is no bridging between ports. So which feature is required to make this connectivity successful? No worries, implementation can be leveraged by powerful features provided in cisco firewall software Redundant interface support. It is just like teaming of nics in server OS like windows , linux etc you can achieve virtual link spanning accross multiple physical links. And providing redundancy so that if one phyiscal link member of redundant interface goes down doesn't hampers communication going on between two devices. And if primary physical links goes down traffic switchover to secondary link is completely transparent. No connectivty loss happens.
Here is how you can make your scenario successful just by simply configuring cisco asa 5510+ using following commands:
Here is the excerpt of cisco asa 5510+ firewall:
!
interface Ethernet1
no nameif
no security-level
no ip address
!
interface Ethernet2
no nameif
no security-level
no ip address
!
interface Redundant1
member-interface Ethernet1
member-interface Ethernet2
nameif inside
security-level 100
ip address 10.10.10.1 255.255.255.252
!
Now you can also check which physical interface is primary which belongs to redundant interface:
hostname# show interface redundant number detail | grep Member
Now how to make one of the physical interface active here is how you can make it:
hostname# redundant-interface redundant number active-member physical_interface
Here is how you can make your scenario successful just by simply configuring cisco asa 5510+ using following commands:
Here is the excerpt of cisco asa 5510+ firewall:
!
interface Ethernet1
no nameif
no security-level
no ip address
!
interface Ethernet2
no nameif
no security-level
no ip address
!
interface Redundant1
member-interface Ethernet1
member-interface Ethernet2
nameif inside
security-level 100
ip address 10.10.10.1 255.255.255.252
!
Now you can also check which physical interface is primary which belongs to redundant interface:
hostname# show interface redundant number detail | grep Member
Now how to make one of the physical interface active here is how you can make it:
hostname# redundant-interface redundant number active-member physical_interface
Friday, March 12, 2010
BGP BASIC CONFIGURATION
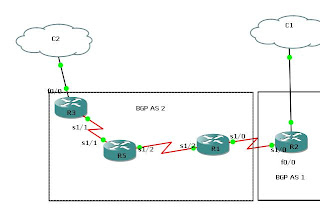
Configuration of BGPv4 is simple on Cisco. Here in this scenario R2 is on AS 1 and rest of the other routers i.e. R1,R5 and R3 are on AS 2.
Configuration Objective is to achieve inter AS communication. Simple BGP configuration neigbourship and broadcasting network. LANs shown as clouds C1 and C2.
Internet is connected through C2 cloud. Actually I used DSL modem located in C2 clound. And put routes into it for 192.168.56.0/24 towards R3. So that returning traffic can come in 192.168.56.0/24 network.
In C1 cloud I used VM OS to test all connectivity.
Traffic from VM OS passess through AS 1,AS 2 and to internet. Here is the trace from R2 router for e.g. gmail.com.
Version of IOS on all routers 12.4
R2#traceroute gmail.com source f0/0
Type escape sequence to abort.
Tracing the route to gmail.com (72.14.204.83)
1 172.16.1.2 [AS 2] 56 msec 24 msec 48 msec
2 10.1.1.2 [AS 2] 36 msec 44 msec 48 msec
3 10.1.1.6 [AS 2] 24 msec 48 msec 64 msec
4 * * * #DSL Hop found
5 59.95.96.1 [AS 2] 128 msec 156 msec 136 msec
6 218.248.255.90 [AS 2] 124 msec 140 msec 148 msec
7 121.244.78.166 [AS 2] 116 msec 136 msec 172 msec
8 59.163.25.242 [AS 2] 116 msec 148 msec 148 msec
9 121.240.0.18 [AS 2] 156 msec 140 msec 152 msec
10 216.239.43.214 [AS 2] 124 msec 148 msec 132 msec
11 72.14.232.93 [AS 2] [MPLS: Label 697405 Exp 4] 216 msec
72.14.232.100 [AS 2] [MPLS: Label 391761 Exp 4] 168 msec 160 msec
12 66.249.94.74 [AS 2] 228 msec
66.249.94.72 [AS 2] 200 msec
66.249.94.74 [AS 2] 252 msec
13 209.85.254.155 [AS 2] [MPLS: Label 509864 Exp 4] 500 msec
72.14.232.115 [AS 2] [MPLS: Label 416579 Exp 4] 432 msec
209.85.254.155 [AS 2] [MPLS: Label 520248 Exp 4] 464 msec
14 209.85.255.59 [AS 2] [MPLS: Label 481915 Exp 4] 464 msec 460 msec 480 msec
15 216.239.43.212 [AS 2] [MPLS: Label 729408 Exp 4] 468 msec 476 msec 448 msec
16 209.85.241.210 [AS 2] [MPLS: Label 780964 Exp 4] 448 msec
216.239.43.81 [AS 2] [MPLS: Label 715357 Exp 4] 420 msec 432 msec
17 209.85.248.222 [AS 2] 460 msec 584 msec 472 msec
18 66.249.94.54 [AS 2] 416 msec
209.85.242.209 [AS 2] [MPLS: Label 752323 Exp 4] 444 msec
209.85.248.222 [AS 2] 432 msec
19 72.14.204.83 [AS 2] 440 msec 436 msec 452 msec
and from VM OS:
C:\>tracert -d gmail.com
Tracing route to gmail.com [72.14.204.19]
over a maximum of 30 hops:
1 70 ms 17 ms 2 ms 192.168.56.2
2 35 ms 40 ms 10 ms 172.16.1.2
3 37 ms 27 ms 49 ms 10.1.1.2
4 51 ms 27 ms 19 ms 10.1.1.6
5 * * * Request timed out. #this hop is the DSL modem connected
6 151 ms 147 ms 147 ms 59.95.96.1
7 145 ms 180 ms 169 ms 218.248.255.90
8 143 ms 124 ms 130 ms 115.113.128.17
9 134 ms 126 ms 122 ms 59.163.25.242
10 223 ms 135 ms 126 ms 121.240.0.18
11 124 ms 134 ms 127 ms 216.239.43.214
12 158 ms 188 ms 174 ms 72.14.232.93
13 187 ms 189 ms 215 ms 66.249.94.74
14 498 ms 455 ms 422 ms 209.85.254.155
15 492 ms 429 ms 444 ms 209.85.255.37
16 453 ms 431 ms 433 ms 216.239.43.212
17 426 ms 431 ms 459 ms 216.239.43.81
18 446 ms 432 ms 431 ms 209.85.248.222
19 429 ms 490 ms 429 ms 209.85.242.209
20 458 ms 486 ms 433 ms 72.14.204.19
Trace complete.
First We focus on R2. This router resides in AS 1 as a whole.
Its configuration is as follow:
interface FastEthernet0/0
ip address 192.168.56.2 255.255.255.0
duplex auto
speed auto
interface Serial1/0
ip address 172.16.1.1 255.255.255.252
serial restart-delay 0
router bgp 1
no synchronization
bgp log-neighbor-changes
redistribute connected route-map allowed
neighbor 172.16.1.2 remote-as 2
no auto-summary
! Only these routes will be broadcasted
ip access-list standard allowed
permit 192.168.56.0
route-map allowed permit 10
match ip address allowed
Configuration of R1
interface Loopback0
ip address 10.81.199.1 255.255.255.255
interface Serial1/0
ip address 172.16.1.2 255.255.255.252
serial restart-delay 0
interface Serial1/2
ip address 10.1.1.1 255.255.255.252
serial restart-delay 0
! IGP for intra AS domain routing
router ospf 1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 10.81.199.0 0.0.0.255 area 0
router bgp 2
! Will not rely on IGP for routes
no synchronization
bgp log-neighbor-changes
!Neigbor relationship
neighbor 10.81.199.2 remote-as 2
! update source will be lo0
neighbor 10.81.199.2 update-source Loopback0
!for routes to be seen from iBGP hop coming from eBGP hop
neighbor 10.81.199.2 next-hop-self
neighbor 10.81.199.3 remote-as 2
neighbor 10.81.199.3 update-source Loopback0
neighbor 10.81.199.3 next-hop-self
neighbor 172.16.1.1 remote-as 1
no auto-summary
R5 configuration:
interface Loopback0
ip address 10.81.199.3 255.255.255.255
interface Serial1/1
ip address 10.1.1.5 255.255.255.252
serial restart-delay 0
!
interface Serial1/2
ip address 10.1.1.2 255.255.255.252
serial restart-delay 0
router ospf 1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 10.81.199.0 0.0.0.255 area 0
router bgp 2
no synchronization
bgp log-neighbor-changes
neighbor 10.81.199.1 remote-as 2
neighbor 10.81.199.1 update-source Loopback0
neighbor 10.81.199.2 remote-as 2
neighbor 10.81.199.2 update-source Loopback0
no auto-summary
!
R3 Configuration:
interface Loopback0
ip address 10.81.199.2 255.255.255.255
!
interface FastEthernet0/0
ip address dhcp
duplex auto
speed auto
interface Serial1/1
ip address 10.1.1.6 255.255.255.252
serial restart-delay 0
!
router ospf 1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 10.81.199.0 0.0.0.255 area 0
!
router bgp 2
no synchronization
bgp log-neighbor-changes
! Default route redistributionnetwork 0.0.0.0
network 192.168.1.0
neighbor 10.81.199.1 remote-as 2
neighbor 10.81.199.1 update-source Loopback0
neighbor 10.81.199.3 remote-as 2
neighbor 10.81.199.3 update-source Loopback0
no auto-summary
!
! Default route towards DSL modem
ip route 0.0.0.0 0.0.0.0 192.168.1.1
Sunday, January 3, 2010
Types of NAT on Cisco PIX 525 using Version 8.0
PAT tracking for any source
nat (inside) 1 0.0.0.0 0.0.0.0
global (outside) 1 interface
Dynamic Nating:
nat (inside) 2 192.168.20.0 255.255.255.0
global (outside) 2 192.168.1.20-192.168.1.30 netmask 255.255.255.0
Identity Nating:
nat (inside) 0 192.168.30.0 255.255.255.0
Static Nating:
static (inside,outside) 192.168.1.60 192.168.40.2 netmask 255.255.255.255
Outside Interface:
interface Ethernet1
nameif outside
security-level 0
ip address dhcp setroute
Inside Interface:
interface Ethernet0
nameif inside
security-level 100
ip address 192.168.100.2 255.255.255.0
routes:
route outside 0.0.0.0 0.0.0.0 192.168.1.1 1
route inside 192.168.0.0 255.255.0.0 192.168.100.1 1
Access-lists:
access-list outside_to_inside extended permit tcp any host 192.168.1.60 eq telnet
access-list outside_to_inside extended permit icmp any any echo-reply
applied on:
access-group outside_to_inside in interface outside
Checking translation for each type of translation:
debug icmp trace
show conn
show xlate
Note: There more options for above commands to be used. So explore yourself.
Subscribe to:
Comments (Atom)


